The WELD System
written by
Francis Chan
Introduction
The WELD system is designed with a view to provide a distributed,
concurrent architecture for high-level descriptions and design
exploration. In this paper, we will describe an environment and how
users of this system interact through a browser (user interface) to
view and edit data or information in a collaborative manner over the
network/Internet.
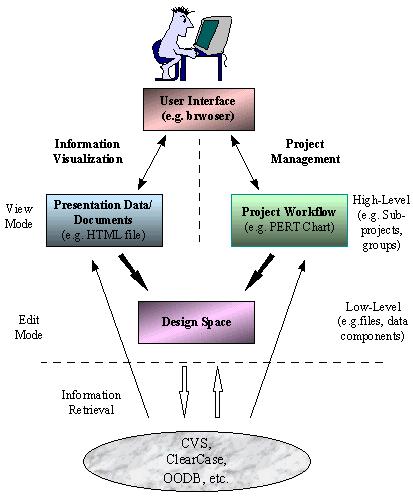
A high-level view of how the different components of
the WELD system interact.
We define two types of usersof the system:
- Viewer who looks at the presentation data and does
editing (locally) in a way that does not affect the global state of
the data.
- Engineer who works on the data in the global state,
possibly in a collaborate fashion with other people over the network.
His changes are recorded and updated and will be reflected next time
(after certain administration procedures such as revision control)
someone accesses the information.
User Interface
In order to promote the exchanging, sharing and leveraging of data, services
and tools that reside over the network, there has to be a common
interface in which users interact with. The Viewer, whose main goal
is to visualize information and perform recording and editing of existing
information needs access to a network interface which could be a
generic browser, such as Netscape or the user interface to the
"Network Computer" which supports the interpretation and display of
presentation data.
Presentation Data
Currently, users of the World Wide Web are provided with static
display of information in the form of text and
graphics or with limited interactivity by means of java and programs
that run on the remote server (Level 0 Client/Server, e.g. cgi-bins,
WebObjects). However, we believe a new
paradigm of information visualization is to emerge where there is a
change from application-centric pages to data-centric documents.
This may be achieved in a number of ways:
- MIME: MIME (Multi-purpose Internet Mail Extensions, the
Internet standard for formatting electronic messages containing not
only text, but other types of data) can be used by HTTP as the encoding
mechanism to pack information into messages. Browsers with specific
configurations can spawn different applications when different kinds of
data are encountered. Example: ghostview and uncompress are called
implicitly when one clicks on a compressed postscript file within a
brwoser in a UNIX environment with the appropriate setting in the
mailcap file.
[WWW Based Structuring of Codesigns]
- Agents and Domains: Agents acts as a personal assistant for
the user invoking tools, libraries, viewers and accessing data on the
user's behalf. The domain, which specifies the environment that the
user works in, is a bounded space template, defined by a set of
relevant description methods, views and actions, and is characterized
by a set of parameters and constraints. This idea could be
extended to faulting in remote applications and/or java applets
whenever necessary for specific applications.
[Information Based Design Environment]
- Intelligent Agents: In addition to performing tasks
for the users, these agents also prompt users for
parameters such as memory, computing power, network bandwidth,
etc.. and communicate with the remote host in determining the optimal
strategy for the user, such as constructing a tailored document, java
applet, or deciding the local vs remote computing/processing ratio for
specific applications (Optimal Level 4 Client/Server).
These models of presentation data would involve extending the present
HTML standard to support embedded commands or developing a new page
description language which will be supported by existing browsers or a
browser that is developed internally.
Project Workflow
The Workflow/Workflow Management application is built to enhance the
productivity and cooperation of engineers by providing project
management modules which help enable the collaboration and
administration of work done over the network. Furthermore, efficient
and intuitive means to tools and services should also be made readily
available to the engineer. The Workflow level can be considered a
high-level view of the design space whose target includes not only
engineers but also non-technical project managers.
Some possible features include:
- Intuitive Workflow Presentation (e.g. PERT chart)
- Group and Personnel Tracking
- Communication Infrastructure (e.g. e-mail, news, etc.)
- Database Support
- Reference/Document Database
- Advanced Search
- Forms Packages
- Automatic Update of Data, Tools and Services
Design Space
The design space forms the integral part of the system. It is the
level where edits and developmental changes are propogated back to the
underlying system and provides a work environment for both the viewer
and engineer.
The design space comprises:
- User: An individual of group having access to a particular part
of a design on the system.
- Data: Any static entity that can be modified. It can be a directory,
file, executable, tool, component, etc..
- Dependency: A symbol (e.g. line or arrow) which demonstrates the
relationships among users and data. This can be generated by the user
himself, through intelligent studying of modules or by interpreting
traces generated by tools, such as VOV (design flow manager).
- Action: A signal indicating an operation (e.g. a person logging
on, editting a file, compilation, etc..)
The design space is where many visualization techniques can be applied
so as to make operations intuitive to the engineer. Coloring schemes
and size of entities could be used to indicate the level of entities'
activities, or how recent data has been updated. Level of detail
could be used to view data up or down a hierachy.
The design space also interfaces with software management tools, such
as RCS, CVS or ClearCase. We hope that by integrating these tools as
the back end, issues relevant to distributed systems such as version
control, configuration management, concurrent updates, etc., could be
solved. However, if integrating an existing
product is not the right solution, we hope that by investigation the
characteristics and capabilities of these tools, we would be able to
implement such control schemes ourselves making use of a
object-oriented database, relevant protocols and transaction
policies.
Issues that have to be resoved include (but are not limited to):
- Security
- Group/Member and Project Registration
Back to Index
Modified: March 13, 1996
Feedback: Francis Chan
(fchan@ic.eecs.berkeley.edu)

